We are currently (again) observing e-mails that are intended to encourage recipients to download files. Those files contain malware that attacks the operating system. The perfidious thing about it: The e-mails contain the content of an earlier e-mail communication, which is intended to establish trust in the authenticity of the message. Our urgent request: Only click on links in e-mails if you are absolutely sure! Look at the sender’s address (not the name, it’s very easy to forge) and the content (is it conclusive?). If you have the slightest doubt, please ask at the URZ: support@hrz.tu-chemnitz.de.
Let’s examine this example:
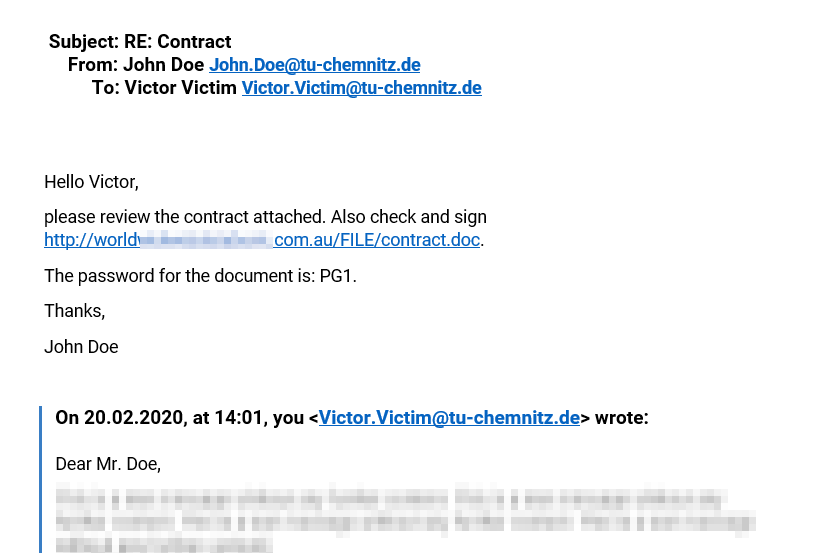
Here John Doe wants you to download an alleged contract that is also encrypted with a password. Behind this is the content of an earlier e-mail exchange – in most cases a long time ago. Would you have hesitated to click the link? If you clicked and then entered the password, your PC or laptop would turn into a remote controllable device for cyber criminals. Therefore, exercise caution and ask if in doubt!
The remaining question is, how did the criminals get hold of the e-mail communication? We can only speculate about this:
- It is possible that Mr. Doe has become a victim of such an attack himself and that his entire e-mail communication is, therefore, open to cyber criminals: either through malware on one of his devices – the Emotet malware is known for such infiltrations – or by passing on his mailbox password.
- Of course, it cannot be ruled out that the same applies to you as the recipient. Minimize this risk by
- changing your password at Chemnitz University of Technology regularly,
- not using your password at Chemnitz University of Technology for other services on the Internet
- using up-to-date anti-virus software (German link only).
- Compromised e-mail servers are also possible prey, of which there are inglorious examples.
Since this type of e-mail is hardly automatically recognizable by spam protection programs, please send us such dubious e-mails (see notes), so that rules for rejection can be built into the DFN mail support. Stay alert!
Confidential E-Mail Communication with S/MIME
Questions to ask yourself, when receiving the email shown above: Can I trust the message, i.e. does the message come from a trustworthy sender and was the message sent by them as well? This trust cannot be established securely with conventional e-mail without cryptographic features – an e-mail is like a postcard: the sender can write any sender address on it, the content can be viewed and changed on the way to delivery. E-mails can only be secured using cryptographic methods. One such method is S/MIME, which is supported by many email programs. You can get the required certificate from the URZ – read our instructions (German link only).

Leave a Reply
You must be logged in to post a comment.